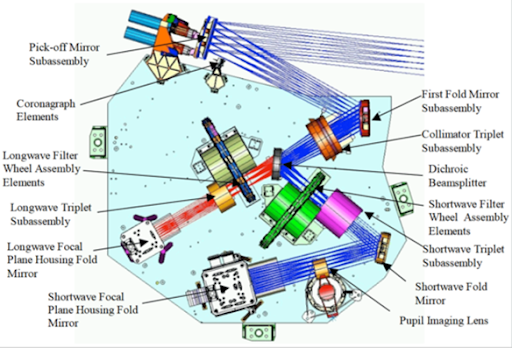
A borderless world means a world without borders, which may or may not be restricted to physical boundaries.
If we consider the physical borders, it can be traced back to when there were only continents and no intra-separation in them. Still, as the population increased, people from different languages, religions, cultures, interests, beliefs, etc., started dividing the continent into several smaller parts to form their community, which led to the formation of 195 countries across the globe. Borders also help to provide security to the citizens from threats and terrorists. Also, even if we consider a borderless world, this will mean that there will be only one leader and only a single constitution to govern all the people, which will lead to instability of the political system. To maintain the political order, if we appoint some officers to keep a check on it and who are approachable to the ordinary people, it becomes easier for the people to express their demands and concerns, making it smoother to run a nation. Although it creates a border between the highest authorities and the ordinary people, it becomes easier for the government and the political system to run smoothly.
Compared to these, the creation of borders also leads to uneven distribution of natural resources, which results in some countries having an abundant supply of resources and enjoying a lavish lifestyle and a unique position throughout the world. Still, some countries may depend on other countries for all their needs. Also, the countries that lack specific resources and qualities can come together to become borderless on those grounds as well. This alliance can lead to a strong relationship and bonding between them. Common world threats i.e., pollution, climate change, and terrorism, can easily be solved if nations identify themselves in a global diaspora instead of a country or state and back off with a mentality of “not in my backyard” by developing a borderless mindset in these topics. The borderless world can create savings for the military. There will be only one army for the whole world, and fights between the two borders will be diminished. Although this can take quite a while, some changes have already been happening.
The Schengen Area comprises 26 European countries that have officially abolished all passports and other border control types at their mutual borders.  This area primarily functions as a single jurisdiction for international travel purposes, with a standard visa policy. Even if we consider the example of our own country, some borders divide states on account of various diversity that exists but still, the country is borderless as a whole with a sense of unity in diversity. Globalization has also contributed to a great extent to make the idea of the borderless world possible. It allows freedom of movement of goods, capital, labor, and distribution of resources as per the requirement and necessity. It also allows the countries to show and share their culture. This helps the countries to develop a strong relationship between them.
This area primarily functions as a single jurisdiction for international travel purposes, with a standard visa policy. Even if we consider the example of our own country, some borders divide states on account of various diversity that exists but still, the country is borderless as a whole with a sense of unity in diversity. Globalization has also contributed to a great extent to make the idea of the borderless world possible. It allows freedom of movement of goods, capital, labor, and distribution of resources as per the requirement and necessity. It also allows the countries to show and share their culture. This helps the countries to develop a strong relationship between them.
Now, let’s consider the virtual border. We can indeed say that the world has become entirely borderless in the virtual space, where people from across the globe can share their ideas, thoughts, projects, concerns, and interests, which have been made possible through the advent of the internet. It has also turned out to be beneficial to the businesses where they have been upscaled from the local to the global scale. They can now reach international clients and expand their business globally. It has also made it possible for the companies to hire internationally and even expand their company globally to get a massive number of people. But it is also true that if the activities of the people are not checked, then this borderless virtual world could turn into complete chaos and could do a lot of damage as well. Although there are cybercrime authorities available to keep a check on the activities of the people, again, we could still see the disastrous effects of this borderless virtual world. For example, The 2016 DDoS Apocalypse. What made this particular case so extreme and widely effective was its target. The Dyn attack was perpetrated by a zombie botnet army. It left users in North America and part of Europe with no net access for hours. The horrifying thing about this attack is that the botnet did not consist of PCs but of the internet of things devices infected with malware called Mirai. Internet of things devices are of significant concern to cybersecurity experts since so many of them are weak against hacking. There are also dangerous individual hackers, such as Mafiaboy (Michael Calce), Iceman (Max vision), and many more who can do critical financial damage or a complete blackout in the country or whatnot.
Internet of things devices are of significant concern to cybersecurity experts since so many of them are weak against hacking. There are also dangerous individual hackers, such as Mafiaboy (Michael Calce), Iceman (Max vision), and many more who can do critical financial damage or a complete blackout in the country or whatnot.
So we can conclude that the borderless world is a dream of a peaceful and unified world that comes with several challenges. Even if the people want to have a borderless world, then to what extent do they want to make it borderless…? It depends on the perspective of how people use the concept of the “borderless world” and whether they think that it is necessary to have one.