- by Aman Pandey
Being in a technical club, we often discuss about innovation 💡 . Anyways, it is not just about being in a tech club 🔧 it is all about being a visionary, you frequently ponder into the thoughts of How an Idea come into existence ❓
Ever thought about actually making a solution and creating its “actual” value 💸. (don’t care, it’s just an emoji). Value is not always about money, it about how much and how great effect it is making on the lives of this magnificient earth 🌏 . Money is just a side effect of creating value.
" A very simple definition of innovation 💡 can be thought of as A match between the SOLUTION 🔑 & the NEED 🔒 that creates some form of VALUE. "
It is all about the game of a GOOD Product strategy, that turns the solution into a value.
Whenever a new solution is launched for the society, it curbs across a different set of people 👥 👤 . Infact there’s a chart which will explain the things better than anything else.
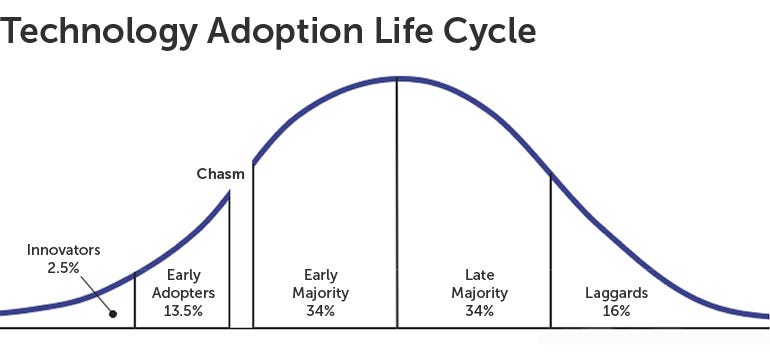
You see the first portion of the curve? The Innovators? These are more of a tech enthusiasts 📟 who are crazy about any new technology, and just want to innovate. Then the Early Adopters ☎️, who actually see some value in the solution. These are the Visionaries 📣 . They are willing to see through business and value of a solution. Then comes the Early Majority, known as the Pragmatist 😷 , they are the first adopters of a technology in the market. They always seek out to improve their companies’ works by obtaining the new technology. Rest are the Late Majority, popularly known as skeptics, they usually look out for recommendations and then the Laggards, idk what they are called.
So there are certain strategies involved in the phases of transiting an innovation to a startup and to a company. This processs is known as Customer Development.
Oh wait ⚠️, looks like we forgot something.
You see a little gap 🌉 between the early adopters and the early majority, The Chasm. This is prolly the hardest and most important bridge that a solution needs to cover in order to create its value 💸 .
There are many startups which might make to that side of chasm, and the startups which might not make. In the most common terms, the first set of customers/buyers of your tech, who agrees to give a try on your innovation.
But, let us keep it for some other time.
Now the stuff, might depend upon certain criteria.
- There already exists some market and you want to capture that market.
- There are several markets, and you want to Re-Segment them according to your innovation.
- You don’t have any market, i.e. you create your own for your product.
But this is the talk of some other time. Let’s pretend we are not going deep into this. We know that, we have a market, which already have customers, a market which exists but isn’t used, and the market, which is still out of existence. You understand the difficulty in all the cases right. 📈
Baghai, Coley, and White came up with something in 2000, called as the Three Horizons of Innovation., more formally known as McKinsey’s Three Horizon of Innovation.
Let us now understand this, with a little example of Sleep medicine industry. 💊
According to a study, in America, around 5~10% population is affected by insomnia, and 2-4% by Sleep Apnea. So, there is already a good market.
Now, the disruption in sleep medicine industry led to a several researches 🔎.
One research was super disruptive, the innovation of Transcranial System.
After a lot of researches on its subjects, collecting data through fitbands, and devices like Beddit which were kept under the mattress of the subject, the researchers collected a lot of data about sleeping patterns. The researchers 🔎, came with the solution of Transcranial systems, which is a device, in which changing magnetic fields stimulates the brain signals and lets you sleep.

Source: Wikipedia
And most of all, this is an non invasive device, i.e. it need not to be planted inside your brain. How do you think the researchers were able to do this?
Well this is all because of Artificial Intelligence.
- The wrists bands ⌚️ used to monitor sleep activities. The fitbit bands accumulated around 7 billion nights of sleep😪.
- The beddit devices, were kept under the mattresses, that records your pulses(could not record your oxygen levels though).
- Apple🍎 watches, are so sharp in their tracking systems, that sometimes they are used as medical diagnosis devices.
So, what transcranial systems do, they track the abnormal pattern in the sleep signals, and send electrical signals, to let the person sleep comfortably.
Now there’s a bigger picture to understand here. If such a solution exists, then why ❓ is it not being used.
To understand this, let us now see the 3 horizon of Innovations:

The horizontal axis, is about how new the innovation is, and the vertical axis is about the novelty of the market, that if the users already exists.
-> The Trancranial System lies, somewhere in the bottom right, where we know the existing market, which in this case are the APNEA patients, but the tech is still new to be used.
This makes it a bit difficult to convert this innovation to a company. 🎬
This still needs a lot of research and finally the makers have to tamper the already existing market, and bring in their device.
Let us take one more example. Support your plan to make a device, that tracks the breathing patterns or pulse rate, and you get data on your mobile phone. Now this data, after going through a series of AI models, lets the Doctor diagnose the severity of the disease and correctly cure you. ⭕️
In this case, you know the solution, and exactly what might solve your problem. Plus hand, you know the target customers. So is possible that this product can be shipped like in the next month.
This App lies somewhere in the lower left.
Now, let me clarify something for you.
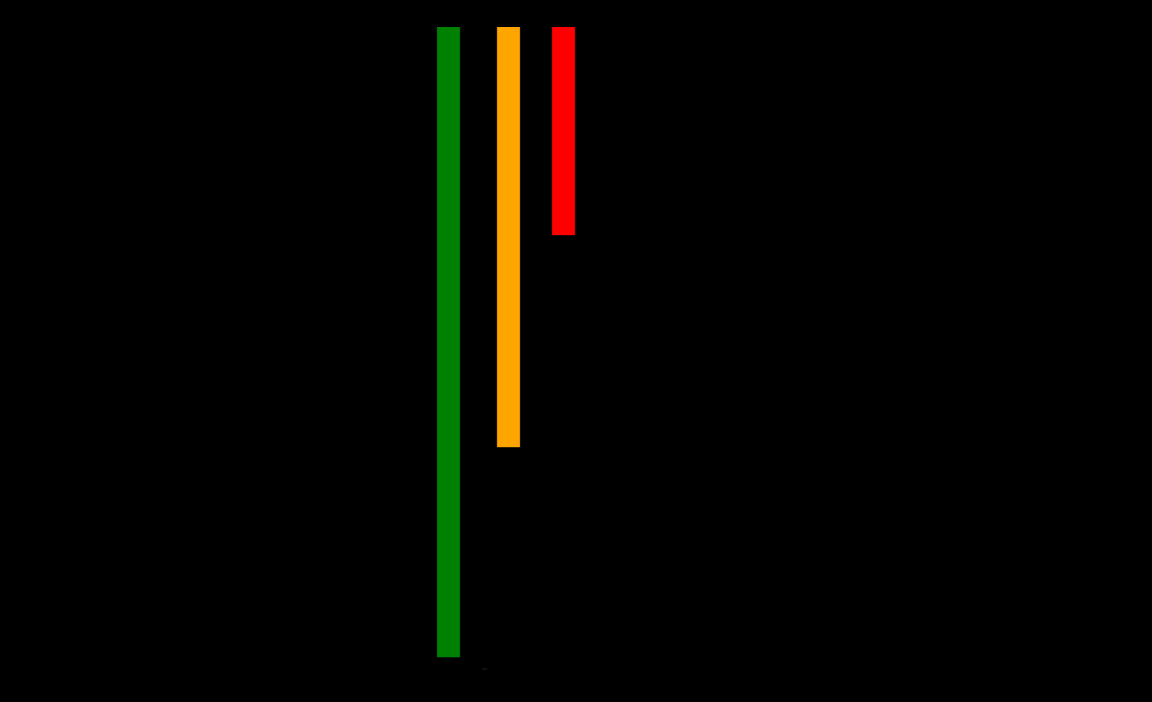
- Horizon 1 is considered to be of Not Much risk ⚪️, and these just need the improvements and cost reductions from the item the customer used before this (because you are targeting already existing customers)
- Horizon 2 is the More Risk zone🔵 , and thus should be approached with care
- Horizon 3 is the Highest risk zone 🔴, and you never know, whether the innovation will be able to even make it to that side or not. And might even take next 5 years to come into proper existence.
So, looking at the picture, from the farther point, we spot a sense of the patience and efforts required to give an innovation, a value.
Just like, Apple beat blackberry by making a device which served more as a personal device, unlike Blackberry which focused only on business users. So, in a short span of time, just in 2 years after launching iPhone in 2007, it took over Blackberry as the leading Mobile phone seller in the world.
You have to be a visionary to understand it.
Thank You.
Courtesy: CHRISTIAN TERWIESCH