author: aman
Blog I - Part IV - Day 04
The process to create a secure system, requires the knowledge of almost every domain in periphery of the application you are making, and the conjunction of that every technology. For eg. working on a Blockchain systems requires you to have an idea about what goes on in the Distibuted networks, the data structures, the contract flow, the cryptographic key generation, and a lot more.
The most important thing to create a secure system is reaching out to the edges of the softwares use cases, the absolute critical thinking. This blog covers a few very basic challenges faced in making and checking the softwares build. Following blogs will then cover the terms, very important to create great security softwares. We'll also cover(at the end of this BIG blog), the working of a few good analysers and bug finders.
Let's get on ramp...
In this micro-blog
- What am I talking about?
- Why am I talking about it?
- Have you heard before? (The "goto fail;", Heartbeat, Meltdown, Spectre)
- What the world is upto against such ____ ?
- Basic Challenges faced
- Unimportant sounding complete terms
- Motivation behind
Basic Challenges faced
It is really simple to understand how does a program analyser works? It is a pretty vague and straight approach. There is a code that you want to check and certain "specifications" for what you want to look into the program. These specifications are also known as invariants. In mathematics, invariants are the properties of any "object" that remains unchanged.
Leaving a very short note here as I have not discussed about Formal languages and methods, "In formal languages, the invariants can be used to prove, what is called as correctness".
Chuck the above line off for a while.
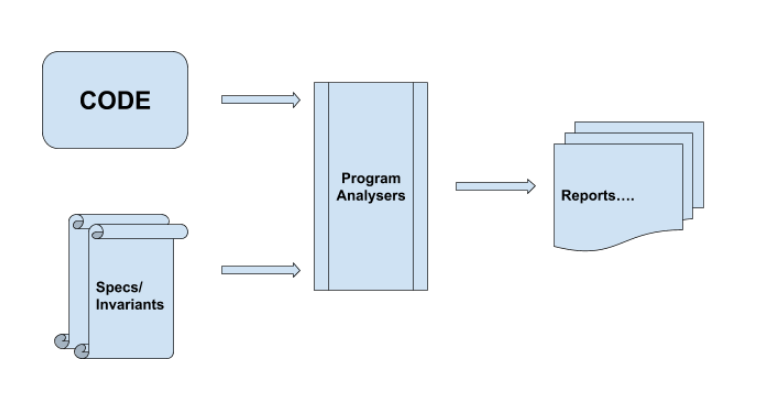
This is simply what a program analyser does.
Now what will a program analyser be exactly working on. As a simple guess, it will "detect" a certain inputs for the feeded program -> check the program for crashing -> show reports.
This works easily for a simple 10 line code, but, what if the program goes ~10,000 lines, and a variety of input cases and boundary conditions. And the biggest doubt, How will you make the analyser to "detect" the inputs?.
Machine Learning?
Nah, this is no Machine Learning. Though it could carry an application of Machine Learning.
understanding challenges
Look at the following code, this will help you comprehend the further blog.
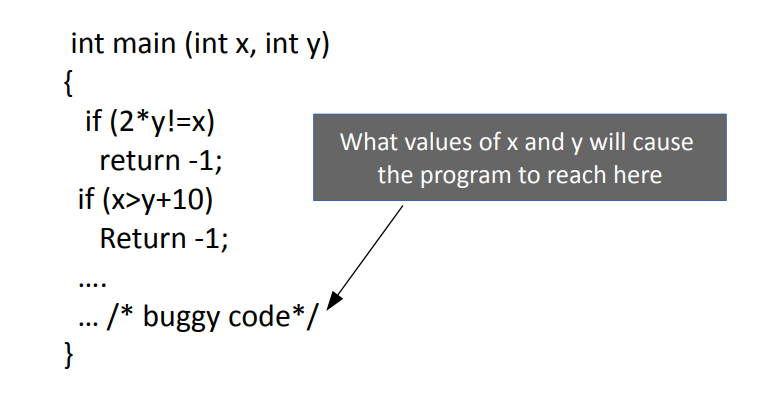
Suppose, we try to analyse this program by finding various paths that can be generated by different sets of inputs.
But,
How will we able to find different inputs that will take different various paths?
And, even we are able to write different inputs. Are we going to write those inputs manually?
No! not at all. These are the challenges, solved very gracefully.
Future blogs, will cover those techniques as well.
Lets keep the drill on and dive further.
Cheers!!!
