IoT Overview
We are living in a world where technology is developing exponentially. You might have heard the word IoT, Internet of Things. You might have heard about driverless cars, smart homes, wearables.
The Internet of things is a system of interrelated computing devices, mechanical and digital machines provided with unique identifiers and the ability to transfer data over a network without requiring human-to-human or human-to-computer interaction
IoT is also used in many places such as farms, hospitals, industries. You might have heard about smart city projects too (in India). We are using lots of sensors, embedded systems, microcontrollers and lots of other devices connecting them to the internet to use those data and improve our current technology.
Our sensors will capture lots of data and it will be used further depending on the user or owner. But what if I say this technology can be harmful too? It may or may not be safe to use it. How?
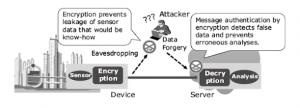
These data transferring from using IoT from source to its destination can be intercepted in between and can be altered too. It can be harmful if the data is very important, For ex. Reports of a patient generated using IoT can be intercepted and altered so the doctor can not give the correct treatment to the patient. Also, some IoT devices can be used by the Army transferring very secret data. If it can get leaked, then it can create trouble for the whole country.
The Information-technology Promotion Agency of Japan (IPA) has ranked “Exteriorization of the vulnerability of IoT devices” as 8th in its report entitled “The 10 Major Security Threats”.
So, can we just stop using IoT? No, we can’t. We have to secure our data or encrypt our data so the eavesdropper can never know what we are transferring.
Cryptography Overview :
Cryptography is a method of Protecting information and communications through the use of codes, so that only those for whom the information is intended can read and process it.
There are mainly two types of encryption methods.
- Symmetric key
- Asymmetric key
Symmetric key uses the same secret key to encrypt or decrypt data while Asymmetric key has one public key and one private key. A public key is used to encrypt data and it is not a secret, anyone can have it and use it to encrypt data but only a private key (of the same person whose public key was used) can be used to decrypt that plaintext.
In Cryptography, We usually have a plaintext and we use some functions, tables and keys to generate ciphertext depending on our encryption method. Also In order to make our data exchange totally secure, we need a good block cypher, secure key exchange algorithm, hash algorithm and a message authentication code.
Block cipher – It is a computable algorithm to encrypt a plaintext block-wise using a symmetric key.
Key Exchange Algorithm – It is a method to share a secret key between two parties in order to allow the use of a cryptography algorithm.
Hash Algorithm – It is a function that converts a data string into a numeric string output of fixed length. The hash data is much much smaller than the original data. This can be used to produce message authentication schemes.
Message Authentication Code (MAC) – It is a piece of information used to authenticate the message. Or in simple words, to check that the message came from the expected sender and the message has not been changed by any eavesdropper.
NOTE: you might wonder why we don’t just send data using key exchange algorithms when it is reliable to share secret keys. You can search for it or tell you in short. It is neither reliable nor secure to share data using key exchange algorithms.
LightWeight Cryptography:
Encryption is already applied at the data link layer of communication systems such as the cellphone. Even in such a case, encryption in the application layer is effective in providing end-to-end data protection from the device to the server and to ensure security independently from the communication system. Then encryption must be applied at the processor processing the application and on unused resources and hence should desirably be as lightweight as possible.
There are several constraints required to achieve encryption in IoT.
- Power Consumption
- Size of RAM / ROM
- Size of the device
- Throughput, Delay
Embedded systems are available in the market with 8bit, 16-bit or 32-bit processors. They have their own uses. Suppose we have implemented a system of Automated doors which open and close automatically at a bank. Which also counts how many people entered or left the bank. We want to keep this record secret and store it on the cloud. Using a 1GB RAM, 32bit / 64bit processor with a very good ROM just to ensure the privacy of data doesn’t make sense here. Because we will need a good space to install our setup, we will need to spend a lot more money than we should while this thing can be achieved with cheaper RAM, ROM and processor.
Keeping the above points in mind, implementing conventional cryptography in IoT which are used for Mobile Phones, Tablet, Laptop / PC, Server is not possible. We have to develop a separate field “Lightweight Cryptography” which can be used in Sensor networks, Embedded systems etc.
Applying encryption to sensor devices means the implementation of data protection for confidentiality and integrity, which can be an effective countermeasure against the threats. Lightweight cryptography has the function of enabling the application of secure encryption, even for devices with limited resources.
Talking about AES, It usually takes 128bit long keys with 128 lock size. It uses 10 rounds of different steps like subbytes, shift rows, mix columns and add round keys. Implementing this requires a good amount of space, processing speed and power. We can implement it in IoT with reduced length of key or length of the blocksize but then it will take less than 30 minutes to break AES.
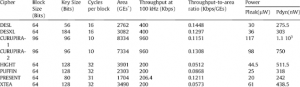
There are many Lightweight cryptography algorithms developed like TWINE, PRESENT, HEIGHT etc. Discussing all of them requires a series of blogs but I am adding a table showing a comparison of some Lightweight Cryptography. You can observe changes in block size from 64 to 96 can create a huge difference in power consumption and area requirement.
Lightweight cryptography has received increasing attention from both academic and industry in the past two decades. There is no standard lightweight cryptosystem like we have AES in conventional cryptography. Research is still going on. You can get updates of the progress at https://csrc.nist.gov/Projects/lightweight-cryptography.
The whole idea behind this blog is to discuss lightweight cryptography and overview of it. 🙂
Author: Aman Gondaliya
Keep reading, keep learning!
TEAM CEV